|
Buy Wii games and accessories at GameStop. Shop our huge selection of new and used Wii games and accessories. How to Get Free Wii Games. Free games? Doesn't that go against everything that's right and natural? Perhaps, but a number of websites collect games that are playable on your Wii, with your Wii controllers. They're not as. Free Wii games and burn them to DVDR Install homebrew 4.2. Follow. 2. http:// to save you some time but check it out, works for all my games, got so many I don't even play them all. Share; Report. Wii U from Nintendo - Official Site. We noticed that your account's country setting is set to Canada, but you're viewing the U. S. version of Nintendo. If you’d like to purchase a game or see product details for your region, please switch to the Canadian version of the site.  
Join our free rewards program today. What is My Nintendo? Rewards. Missions. About points. Play Nintendo. Fun stuff for kids! Friends. Explore. News & tips. and plays your Wii games, too! Buy Now $ 299. 99 MSRP* Comic. . regardless of tastes. Whilst many titles utilised the unique Wii motion controls. there were plenty of other great games available on the Wii. the majority of them were released by Nintendo. How To Download And Copy Wii Games & Play Homebrew, No Mod Chip. you can download and copy wii games and you can burn backup disks and play them freely. how to download wii games and burn them to a DVD.
0 Comments
Epub Metadata Subtitle SearchSigil v. 0. 9. 6 繁體中文版 - 所見即所得的 EPUB 電子書編輯軟體Sigil 是一款跨平台且開放原始碼的 epub 電子書編輯軟體,所見即所得,且可直接編輯程式碼 (代碼)。這款免費軟體的主要功能和特色如下:提供線上使用者導覽 (使用手冊) 和維基文件;跨平台:可在 Windows、Linux 和 Mac 上執行;完全支援 UTF- 1. EPUB 2 規格;提供多重檢視模式:書本檢視、代碼檢視和預覽;在書本檢視模式下可進行所見即所得的編輯;在代碼檢視模式下可完全掌控直接編輯的 EPUB 語法;目錄產生器,支援從 H1 到 H6 共 6 級標題;中繼資料 (Metadata) 編輯器,完全支援所有可能的中繼資料項目 (超過 2. EPUB 和 HTML 檔案、圖片和樣式表;整合 Flight. Crew EPUB 驗證程式,可讓使用者驗證文件是否 EPUB 相容;注意:程式啟動後為英文介面,請從功能表的 Edit → Preferences → Language,在 User Interface Language 和 Default Language for Metadata 的下拉式選單中皆選取 Chinese – Taiwan,程式重新啟動後即為繁體中文介面。§ 作業系統:Windows Vista/7/8/1. Screenshot)§ 官方網站下載頁面§ 檔案下載Sigil 原文簡介:Sigil is a multi- platform EPUB ebook with the following features: Online Sigil User’s Guide, and Wiki documentation. Multi- platform: runs on Windows, Linux and Mac. Full UTF- 1. 6 support. Full EPUB 2 spec support. Multiple Views: Book View, Code View and Preview View. WYSIWYG editing in Book View.

Karen Coyle's writings on the challenges libraries face in the age of digital communication, including censorship, privacy and intellectual property issues. Sigil 是一款跨平台且開放原始碼的 epub 電子書編輯軟體,所見即所得,且可直接編輯程式碼 (代碼)。這款免費軟體的功能和. Over the years we have had some complaints about calibre's appearance. We have had just as many appreciative emails from people loving the look. EPUB Publications 3.0 EPUB is an interchange and delivery format for digital publications based on XML and Web Standards. EPUB 3, the third major revision of EPUB, is. Complete control over directly editing EPUB syntax in Code View. Table of Contents generator with multi- level heading support. Metadata editor with full support for all possible metadata entries with full descriptions for each. User interface translated into many languages. Spell checking with default and user configurable dictionaries. Full Regular Expression (PCRE) support for Find & Replace. Supports import of EPUB and HTML files, images, and style sheets. Documents can be validated for EPUB compliance with the integrated Flight. Crew EPUB validator. To use AVG Internet Security for free up to 2/26/2018, just download and install the latest version of AVG Internet Security setup installer from AVG paid version installation file download page:(http://www.avg.com. Is Your Free AV a System Hog?: Page 2. Antivirus software is a necessity these days but some solutions are a bigger drain on system resources than others. See how AVG, Microsoft, Avast and Comodo compare. If you thought that you don’t need a Antivirus software and you are safe because you don’t visit dodgy websites, think again. I used to think that i knew quite a lot about computers & security and knew what not to click. The posting of advertisements, profanity, or personal attacks is prohibited. Please refer to our CNET Forums policies for details. All submitted content is subject to our Terms of Use. Free Working License Key Serial To Activate AVG Anti- Virus 8 Till 2. Years Subscription Expiry) « My Digital Life. Fed up with free anti- virus solution giveaways with subscription period validity of just 3 months, 6 months or 1 year? Most security product developers nowadays attracts user with several months of free usage promotional offer, and then require user to pay an annual subscription fee to continue using the product or to receive the virus signature update. Instead of succumbing to search for new free license key, serial number or activation code every other few months when the subscription period expires or ends, here’s one license key number like no other, for AVG Anti- Virus users. We receive tip off that the following license number for AVG Anti- Virus will only expire on February 2. YEARS validity and free usage. For AVG lovers who installed AVG Anti- Virus by using the one year free subscription license which going to expire by December 1, 2. AVG is just in time. It’s unclear if the super long activation license key for AVG Anti. Virus is part of what promotion, or it’s a leaked serial key. Anyway, the license number will activate a full version of AVG Anti- Virus 8. There are a total of 1. To use AVG Anti- Virus for free for 1. AVG Anti- Virus setup installer (current version 8. AVG paid version installation file download page. When prompt for license number during installation, enter the following serial key: XXXX- XXXXX- XXXXX- XXXXX- XXXXX- XXXXX- XXXXX (Removed due to copyright infringement notice by AVG)Once installation is completed, AVG Anti- Virus full retail edition will have the license expiry date of 2/2. For users who want the completely free for forever version of anti- virus software, AVG Free Edition 8. Page 1 of 3 - Infected with a virus or a malware - posted in Virus, Trojan, Spyware, and Malware Removal Logs: I recently upgraded AVG (free) and AD-AWARE (free) to their latest versions respectively. For some reason I can not. Figuring Out What Is Causing DISK IO. Tip: It’s likely a caching issue or a compatibility issue with another program. NEVER run two security suites at the same time. If you use AVG uninstall ANY other programs that might. Page 1 of 2 - Cannot connect to Google - posted in Virus, Trojan, Spyware, and Malware Removal Logs: Suddenly the other night I noticed I could no longer connect to google.com. Whenever I try the computer churns for a bit and. AVG Anti- Virus Pro, except that without anti- rootkit and some online security features. Or, it’s possible to opt for AVG Anti- Virus Network Edition 7. Note: No longer valid. Do check out more free antivirus software available. Update: Free AVG Anti- Virus 9. Torrent anonymously with torrshield encrypted vpn pay with bitcoin. Also remember, this test was conducted on the free versions of avast, Panda Cloud, and MSE but on the paid versions of Avira and Bitdefender. So it is goes without saying Bitdefender and Avira has a leg up on the others for. Infected with a virus or a malware. I recently upgraded AVG (free) and AD- AWARE (free) to their latest versions respectively. For some reason I can not connect to the respective servers for updates (Grisoft and Lavasoft). Also, I can not generate an ID Number for AMMYY Admin (it says "error" instead of generating an ID Number). In the case of AVG the error message says: "UPDATING PROGRESS. Update fail. The connection with update server failed. Please follow these steps: make sure internet connection is active... Make sure the connection parameters are set properly". In the case of AD- AWARE, the error message says: "Connection error, check your settings. Error code: - 1)". In the case of AMMYY Admin, the error message says: "error (1. Hxx. P: //RL. AMMYY. COM. Would you like to change proxy setting?"It should be noted that I have no problems browsing the internet, including entering the respective websites of the three companies who provide those softwares (Lavasoft, Grisoft, and AMMYY Admin). It should also be noted that in addition to this computer, I have another computer, as well as a laptop. Using the othe computer and the laptop I do not have a problem updating AVG and AD- AWARE, and no problem generating an ID Number for AMMYY Admin. All three computers are using the same Router. Here is the DDS. txt: DDS (Ver_1. NTFSx. 86 Run by hillel at 2: 1. Thu 0. 2/1. 0/2. 01. Internet Explorer: 6. Microsoft Windows XP Professional 5. GMT - 5: 0. 0]AV: AVG Anti- Virus Free Edition 2. Enabled/Outdated* {1. DDD0. 97- 3. 6FF- 4. F- 9. E1. B- 5. 2D7. D6. BF}AV: Lavasoft Ad- Watch Live! Anti- Virus *Enabled/Updated* {A1. C4. F2. E0- 7. FDE- 4. AFAE- 0. 13. EFC3. EDE3. 3}============== Running Processes ===============C: \PROGRA~1\AVG\AVG1. C: \WINDOWS\system. Dcom. Launchsvchost. C: \WINDOWS\System. C: \Program Files\Ahead\In. CD\In. CDsrv. exe. I: \Program Files\IOGEAR\Wireless USB\Wi. Center. Service. exesvchost. C: \Program Files\Lavasoft\Ad- Aware\AAWService. C: \WINDOWS\system. C: \Program Files\Common Files\Logi. Shrd\LVMVFM\LVPrc. Srv. exesvchost. exe. C: \Program Files\Common Files\Acronis\Schedule. I: \Program Files\IOGEAR\Wireless USB\dfu\al_dfu. C: \Program Files\Common Files\Apple\Mobile Device Support\bin\Apple. Mobile. Device. Service. C: \Program Files\AVG\AVG1. I: \Program Files\IVT Corporation\Blue. Soleil\BTNt. Service. C: \Program Files\Bonjour\m. DNSResponder. exe. C: \WINDOWS\System. DVDRAMSV. exe. C: \WINDOWS\System. C: \Program Files\Norton Go. Back\GBPoll. exe. I: \Program Files\High. Point Technologies, Inc\High. Point RAID Management Software\service\hptsvr. C: \Program Files\Java\jre. I: \Program Files\High. Point Technologies, Inc\High. Point RAID Management Software\service\drvinst. C: \WINDOWS\system. KMDEVMONSRV. exe. C: \WINDOWS\system. KMdevmonx. exe. C: \Program Files\Common Files\Logi. Shrd\LVCOMSER\LVCom. Ser. exe. C: \WINDOWS\System. C: \WINDOWS\system. ZONELABS\vsmon. exe. C: \Program Files\AVG\AVG1. C: \Program Files\Western Digital\WD Drive Manager\WDBtn. Mgr. Svc. exe. C: \Program Files\AVG\AVG1. Identity Protection\Agent\Bin\AVGIDSAgent. C: \Program Files\Canon\CAL\CALMAIN. C: \PROGRA~1\AVG\AVG1. C: \WINDOWS\Explorer. EXEC: \Program Files\AVG\AVG1. C: \Program Files\Hp\HP Software Update\HPWu. Schd. 2. exe. C: \WINDOWS\system. C: \Program Files\Microsoft Intelli. Type Pro\type. 32. C: \Program Files\Acronis\True. Image. Home\True. Image. Monitor. exe. C: \Program Files\Common Files\Acronis\Schedule. C: \Program Files\Acronis\True. Image. Home\Timounter. Monitor. exe. I: \Program Files\i. Tunes\i. Tunes. Helper. C: \Program Files\Common Files\Logi. Shrd\LCom. Mgr\Communications_Helper. C: \Program Files\Western Digital\WD Drive Manager\WDBtn. Mgr. UI. exe. C: \Program Files\Rogers Online Protection\Rogers Servicepoint Agent\Rogers. Servicepoint. Agent. C: \Program Files\Common Files\Java\Java Update\jusched. C: \Program Files\Creative\SBAudigy\Surround Mixer\CTSys. Vol. exe. C: \WINDOWS\system. C: \WINDOWS\system. Rundll. 32. exe. C: \Program Files\AVG\AVG1. I: \Program Files\Gadwin Systems\Print. Screen\Print. Screen. C: \WINDOWS\system. I: \Program Files\Copernic Desktop Search - Home\Desktop. Search. Service. exe. C: \Program Files\i. Pod\bin\i. Pod. Service. C: \Program Files\Creative\Media. Source. 5\Go\CTCMSGo. U. exe. I: \Program Files\HP\Digital Imaging\bin\hpqtra. C: \Program Files\Lavasoft\Ad- Aware\AAWTray. C: \Program Files\Norton Go. Back\GBTray. exe. C: \Program Files\AVG\AVG1. Identity Protection\agent\bin\avgidsmonitor. C: \WINDOWS\system. RAMASST. exe. I: \Program Files\HP\Digital Imaging\bin\hpqgalry. C: \Program Files\Spyware. Guard\sgmain. exe. C: \Program Files\Spyware. Guard\sgbhp. exe. C: \Program Files\Internet Explorer\iexplore. C: \Documents and Settings\hillel\Desktop\dds. Pseudo HJT Report ===============u. Start Page = hxxp: //www. Search Bar = m. Search Bar = u. Internet Settings,Proxy. Override = *. localu. Search. URL,(Default) = hxxp: //www. Winlogon: Userinit=c: \windows\system. BHO: Spyware. Guard. DLBLOCK. CBrowser. Helper: {4a. 36. 8e. TB: & Google: {2. TB: & Robo. Form: {7. TB: Copernic Desktop Search - Home Toolbar: {4a. Toolbar. Container. TB: {4. 2CDD1. BF- 3. FFB- 4. 23. 8- 8. AD1- 7. 85. 9DF0. B1. D6} - No File. TB: {F1. F2. 2D5. CA2. D- 4. C8. A- 9. B- 0. D6. 38. 9DC2. E} - No File. EB: Copernic Desktop Search - Home Toolbar: {4a. Toolbar. Container. EB: Copernic Desktop Search - Home: {9c. Deskband. Integration. EB: {3. 26. 83. 18. No File. EB: {4. 42. DFF- 7. 47. E- 4. EDC- B3. 0C- 7. 87. E5. 0CD0. C} - No File. EB: & Discuss: {bdeade. Run: [Power. Bar] u. Run: [ATI Launchpad] "c: \program files\ati multimedia\main\launch. Pd. EXE"u. Run: [Gadwin Print. Screen 3. 5] i: \program files\gadwin systems\printscreen\Print. Screen. exe /nosplashu. Run: [ctfmon. exe] c: \windows\system. Run: [Copernic Desktop Search - Home] "i: \program files\copernic desktop search - home\Desktop. Search. Service. exe" /trayu. Run: [Flash. Get 3] "c: \program files\flashget network\flashget 3\Flashget. Run: [fsm] u. Run: [Creative Media. Source Go] "c: \program files\creative\mediasource. CTCMSGo. U. exe" /SCBu. Run: [CTReg. Run] c: \windows\CTReg. Run. EXEm. Run: [CTStartup] c: \program files\creative\splash screen\CTEax. Spl. EXE /runm. Run: [HP Software Update] "c: \program files\hp\hp software update\HPWu. Schd. 2. exe"m. Run: [Win. Fax. App. Port. Starter] wfxsnt. Run: [type. 32] "c: \program files\microsoft intellitype pro\type. Run: [True. Image. Monitor. exe] c: \program files\acronis\trueimagehome\True. Image. Monitor. exem. Run: [Script. Sentry] c: \program files\script sentry\Script. Sentry. exe /checkm. Run: [Rox. Watch. Tray] "c: \program files\common files\roxio shared\9. Rox. Watch. Tray. Run: [POINTER] point. Run: [Onelive] m. Run: [Acronis. Timounter. Monitor] c: \program files\acronis\trueimagehome\Timounter. Monitor. exem. Run: [Acronis Scheduler. Service] "c: \program files\common files\acronis\schedule. Run: [Apple. Sync. Notifier] c: \program files\common files\apple\mobile device support\bin\Apple. Sync. Notifier. exem. Run: [i. Tunes. Helper] "i: \program files\itunes\i. Tunes. Helper. exe"m. Run: [Logitech. Communications. Manager] "c: \program files\common files\logishrd\lcommgr\Communications_Helper. Run: [Quick. Time Task] "i: \program files\quicktime\qttask. Run: [SPAMfighter Agent] "f: \program files\spamfighter\SFAgent. Run: [ATIPTA] c: \program files\ati technologies\ati control panel\atiptaxx. Run: [WD Drive Manager] c: \program files\western digital\wd drive manager\WDBtn. Mgr. UI. exem. Run: [Malwarebytes Anti- Malware (reboot)] "i: \program files\malwarebytes' anti- malware\mbam. Run: [Rogers. Servicepoint. Agent. exe] "c: \program files\rogers online protection\rogers servicepoint agent\Rogers. Servicepoint. Agent. AUTORUNm. Run: [Sun. Java. Update. Sched] "c: \program files\common files\java\java update\jusched. Run: [CTSys. Vol] c: \program files\creative\sbaudigy\surround mixer\CTSys. Vol. exe /rm. Run: [P1. Helper] Rundll. 32 P1. P1. 7Helperm. Run: [Upd. Reg] c: \windows\Upd. Reg. EXEm. Run: [AVG_TRAY] c: \program files\avg\avg. Run. Once: [Run. Narrator] Narrator. Startup. Folder: c: \docume~1\hillel\startm~1\programs\startup\spywar~1. Startup. Folder: c: \docume~1\hillel\startm~1\programs\startup\webshots. Launcher. exe. Startup. Folder: c: \docume~1\alluse~1\startm~1\programs\startup\hpdigi~1. Startup. Folder: c: \docume~1\alluse~1\startm~1\programs\startup\hpimag~1. Startup. Folder: c: \docume~1\alluse~1\startm~1\programs\startup\norton~1. GBTray. exe. Startup. Folder: c: \docume~1\alluse~1\startm~1\programs\startup\panaso~1. Status. Mon. exe. Startup. Folder: c: \docume~1\alluse~1\startm~1\programs\startup\ramasst. RAMASST. exe. Startup. Folder: c: \docume~1\alluse~1\startm~1\programs\startup\zoneal~1. Policies- explorer: < NO NAME> = IE: & Google Search - c: \program files\google\Google. Toolbar_en_2. 0. 1. IE: Backward & Links - c: \program files\google\Google. Toolbar_en_2. 0. 1. IE: Cac& hed Snapshot of Page - c: \program files\google\Google. Toolbar_en_2. 0. 1. IE: Customize Menu - file: //c: \program files\siber systems\ai roboform\Robo. Form. Com. Customize. IEMenu. html. IE: Download all with Free Download Manager - file: //i: \program files\free download manager\dlall. IE: Download selected with Free Download Manager - file: //i: \program files\free download manager\dlselected. IE: Download Video - http: //www. IE: Download video with Free Download Manager - file: //i: \program files\free download manager\dlfvideo. IE: Download with Free Download Manager - file: //i: \program files\free download manager\dllink. IE: E& xport to Microsoft Excel - c: \progra~1\micros~4\office. EXCEL. EXE/3. 00. IE: Fill Forms - file: //c: \program files\siber systems\ai roboform\Robo. Form. Com. Fill. Forms. IE: Robo. Form Toolbar - file: //c: \program files\siber systems\ai roboform\Robo. Form. Com. Show. Toolbar. IE: Save Forms - file: //c: \program files\siber systems\ai roboform\Robo. Form. Com. Save. Pass. IE: Si& milar Pages - c: \program files\google\Google. Toolbar_en_2. 0. 1. Professor Emeritus Gerald Fridman is a Fellow of the Royal Society of Canada and one of Canada's foremost legal scholars and authors. After publication of the first edition of The Law of Torts in Canada, he was awarded the. Selected archives: Full-texts of selected scholarly writings on the CISG and the UNIDROIT Principles of International Commercial Contracts and the Principles of European Contract Law. The archives contain full texts of law. 
'But what, after all, is a law? […] When I say that the object of laws is always general, I mean that law considers subjects en masse and actions in the abstract, and never a particular person or action. […] On this view. The www.eprocurement.gov.in platform provides its members with access to several online tenders published by the departments. The Tender Management Software helps buyers and suppliers to reduce the cycle time, unnecessary. Law Commission. 12th July 2. The Law Commission’s Annual Report 2. Most significantly this year we have welcomed a new Chairman, Sir David Bean, who joined the Commission on 1 August 2. We appointed Professor Nick Hopkins as Commissioner for property, family and trust law and extended the … Read more >. The Law of Torts in Canada, 3rd Edition. Professor Emeritus Gerald Fridman is a Fellow of the Royal Society of Canada and one of Canada's foremost legal scholars and authors. After publication of the first edition of The Law of Torts in Canada, he was awarded the Walter Owen Book Prize for distinguished writing on Canadian law. Professor Fridman is the author of several other treatises published by Carswell, among them, The Law of Contract in Canada, 5th Edition, The Sale of Goods in Canada, 5th Edition and Restitution, 2nd Edition. He has been counsel to the firm Cohen Highley LLP for several years, chiefly, but not exclusively, in matters of contract and commercial law. Professor Fridman studied law at St. John's College in Oxford, and holds a B. A., B. C. L. and M. A. from the University of Oxford and a Master of Laws Degree from the University of Adelaide in South Australia. He has been admitted as a barrister- at- law in the Middle Temple in London, England, as a barrister and solicitor of the Supreme Court of South Australia and also as a barrister and solicitor in the provinces of Alberta and Ontario. Welcome to the Wage Determinations OnLine Program! This website provides a single location for federal contracting officers to use in obtaining appropriate Service Contract Act (SCA) and Davis-Bacon Act (DBA. United States Supreme Court Decisions. Cornell Law School’s Legal Information Institute, linked here, provides the best access to cases from 1990 forward. (See Additional Resources below for earlier cases.) The court. A Joint Division of the Institution of Civil Engineers and the South African Institution of Civil Engineering. Independent body set up by Parliament to review and recommend reform of the law in England and Wales. Provides a profile of the Commission and its members with information on their work and a library of publications. 
In addition to having held academic positions at the University of Adelaide, University College at the University of London, the University of Sheffield, the University of Alberta, the University of Western Ontario, as well as being a visiting distinguished professor in the Faculty of Law in the University of Hong Kong, the University of Sydney, the University of Tasmania and the University of Western Australia, Professor Fridman has published 1. He is an expert in the law of contracts, agency, torts, sale of goods and restitution. Erika Chamberlain (LL. B. (Dist.) Western 2. Ph. D. Cambridge 2. Associate Professor and Associate Dean (Academic) in the Faculty of Law at the University of Western Ontario. Prior to her appointment, she served as clerk to Mr. Justice Major at the Supreme Court of Canada and was called to the Ontario Bar in 2. Her teaching and research focus on tort law, equity, and impaired driving law. She has published in leading legal and public health journals, was co- editor of Emerging Issues in Tort Law (2. Tort Law: Challenging Orthodoxy, and co- author of The Law of Torts in Canada, 3rd Edition (2. Dr. Chamberlain was named Professor of the Year by Western Law's Student Legal Society in 2. Stephen G. A. Pitel, (B. A., Carleton; LL. B., Dalhousie; LL. M., Ph. D., Cambridge), is a Professor at the Faculty of Law at Western University. His teaching and research is focused on the conflict of laws, civil procedure, torts and legal ethics. He has co- authored, edited or co- edited fourteen books including Conflict of Laws (2. The Law of Torts in Canada, 3rd Edition (2. He has written many articles on private international law and won several teaching awards. He previously practiced commercial litigation in Toronto. Andrew Botterell has a B. A. from Mc. Gill University, a Ph. D. from MIT, and a J. D. from the University of Toronto. He is currently an Assistant Professor at the University of Western Ontario, where he is jointly appointed to the Faculty of Law and the Department of Philosophy. He served as a law clerk to the Honourable Madam Justice Louise Charron of the Supreme Court of Canada during the 2. Bar of Ontario in 2. Professor Botterell's primary teaching and research interests are in tort law, criminal law, and philosophy of law. Jason W. Neyers has a B. A. (Hon.) from the University of Western Ontario, an LL. B. (Gr. Dist.) from Mc. Gill University, a M. St. from the University of Oxford and is called to the Bar of Ontario. He is an Associate Professor of Law at the University of Western Ontario. Prior to taking up his academic appointment he was a clerk at the Court of Appeal for Ontario. He has published numerous papers and comments in leading law journals and is the co- editor of six books: Understanding Unjust Enrichment (2. The Law of Restitution in Canada: Cases and Materials (2. Cases and Materials on Contract, 3d ed. Emerging Issues in Tort Law (2. Exploring Contract Law (2. Cases and Materials on Contract, 4th ed. He also is the moderator of the Obligations Discussion Group which is an international mailing list devoted to all aspects of the law of obligations. Road signs - Roadwise. Road signs are there to tell you what you ARE allowed to do and what you MUST NOT do. You need to understand road signs and do what they say. Signs giving orders. Traffic and Road Safety Signs in India - Know about the different symbols and rules for road safety and traffic including mandatory, informatory, cautionary signs and. THINK! is the Department of Transport’s dedicated road safety website, with guidance and information for all road-users, along with the latest THINK! TV ads. Grade 2 Requirement 1. Identify and explain 10 important road signs. 2. Tell when and where to cross the road safely. 3. Give road safety rules for. Blue circular signs usually tell you what you must do. Red circular signs usually tell you what you must not do. Signs giving warnings. Signs giving information. SecuritySafetyProducts (Tel 08) Experts in Security Screws, Visitor Books, Call Point Covers, Anti-Slip Tapes, Edge Protection, Safety and Road Signs. Road signs are there to tell you what you ARE allowed to do and what you MUST NOT do. You need to understand road signs and do what they say. Circular signs give. Road safety 1. Road Safety 2. Presented by : Arnel O. Rivera Based on the Presentation Road Safety : Points Hitherto Seldom Noticed by Er. C.J.Johnson MIE.
    
Infinity Blade i. Phone game - free. Download ipa for i. Pad,i. Phone,i. Pod. Your task — to become that hero who will put an end to sufferings of the kingdom. In a powerful chain armor, with a sword and a board in hands you will reach the lonely castle protected by strange beings. On your way you will meet infernal Palladin in front of the castle, a steel robot and also a bodyguard of the king and others, but it will be most difficult to win the most important. You get fireproof points which can be spent for increase in life, capacities, new weapon and armor for each murder. Game possesses stunning graphics! 
Download free Infinity Blade 3: iPhone, iPad and iPod devices are ideally suited for the game. Get Infinity Blade 3 ipa file right now! Infinity Blade II by Chair Entertainment Group, LLC From Epic Games' award-winning studio, ChAIR Entertainment, comes Infinity Blade II, the sequel to the. Read reviews, compare customer ratings, see screenshots, and learn more about Infinity Blade II. Download Infinity Blade II and enjoy it on your iPhone. Infinity Blade for iPhone Cheats - IGN has all the codes, cheat codes, unlockables, easter eggs, achievements, hints, tips and secrets. IGN is the Infinity Blade (iPhone) resource with reviews, wikis, videos, trailers, screenshots, cheats, walkthroughs, previews, news and release dates.Infinity Blade download. Explore o castelo para derrotar todos os seus inimigos: em Infinity Blade, você é o grande guerreiro. Infinity Blade III (3) Guide, Help and Walkthrough By: Chair Entertainment Group, LLC. Download. For help with the Ausar Rising update, see our Ausar Rising guide here. Infinity Wars is a genuine free-to-play trading card game. Play with fully animated cards in 3D battlefields, and assemble decks from over 800 cards and 8 stylized. Download free Infinity Blade: iPhone, iPad and iPod devices are ideally suited for the game. Get Infinity Blade ipa file right now! . and hotfixes from the Windows Update Catalog. Select the location where you want to save the updates. Windows XP Professional. When Windows XP support ends, this is how you secure your PC and save all updates Support for Windows XP has now ended. Microsoft's 8 April support deadline has been and gone and the final security updates for Windows XP have now been released. Worryingly, these updates fixed two critical security flaws that would have allowed hackers to remotely execute code. The final security fixes are part of Microsoft's Patch Tuesday update for 8 April 2. Windows XP will be included. Despite the end of Windows XP support, it is estimated that 2. Many security flaws uncovered in Windows Vista, 7 and 8 may also apply to Windows XP, with hackers potentially able to use Microsoft's own security updates to find new ways of exploiting the ageing operating system. Only Windows 7, with around 4. Windows XP, with the much maligned Windows 8 taking just shy of seven per cent of the OS cake. If you're one of the many Windows XP users out there, the big question is, what happens now support has stopped? There are plenty of articles warning of an incoming hacker storm, as cyber- criminals run riot through unpatched security holes in Windows XP, but how true is this scenario? In this article, we're going to show you how to keep your Windows XP computer safe. WINDOWS XP NO MORE SECURITY PATCHESWhen Windows XP Support ends in April, it means that Microsoft will no longer be issuing any security updates for this operating system. Don't panic, even though Windows XP support ends in April. your computer can still be secure and you can download and save all of the Windows Update files. How to get all XP service packs, updates, etc. together to. I'd have thought setting windows update to. although their files are expanded on c:\windows. WUD integrates itself in the shell in order to simplify installation of UL files. Windows 8.1 Update : x64: 2015-03-25. Windows XP: Service Pack 3: x86. Files to remove from Windows XP to save space. which contains Windows Update download cache. as well as system temporary files. I haven't used XP in a while. The image files are available at the same time as updates that are released on Windows Update. Windows Update website. The ISO image files. Windows XP. 
You'll still be able to download and update patches up to this date, but if a new flaw in the operating system is discovered, it will go unpatched. Potentially, this means that hackers could target the new flaw, letting them infect a Windows XP machine. You'll still be able to install old security updates, but no new patches will be released. This sounds bad, but before you get too worried about Microsoft no longer providing patches, it's important to understand the other threats to your computer. First, other software may have flaws in it, which allows an attacker to infect your computer. Cyber- criminals typically attack well- known bits of software that most people have, so Adobe Reader and Java are typical targets, no matter which version of Windows you're running. Just because Microsoft is going to Windows XP updates doesn't mean other manufacturers will do the same, so you can still update other bits of software. Finally, cyber- criminals use a variety of social engineering tricks to get you to install dodgy software or give them access to your accounts. While AV suites will detect some of these threats, they don't detect everything and certainly won't stop you passing on your username and password over the phone. In this regard, whether or not Microsoft has released new updates for Windows XP or not makes no difference to your security. As you can see, then, Microsoft's decision to stop releasing updates for Windows XP is actually only one part of the security puzzle. This is good news, as it means it's still possible to defend your computer against threats, as we'll show you. WINDOWS XP EXISTING UPDATESWe've talked to Microsoft and it has confirmed that all existing security patches and updates for Windows XP will still be available after support officially ends. Windows XP: Save Windows Update Downloads. Press the Browse button to browse for a folder on your system/network where you want to save the files. CNET; Computers; Delete Windows update files to regain. next to Windows Update Cleanup and any other files you. Delete Windows update files to. 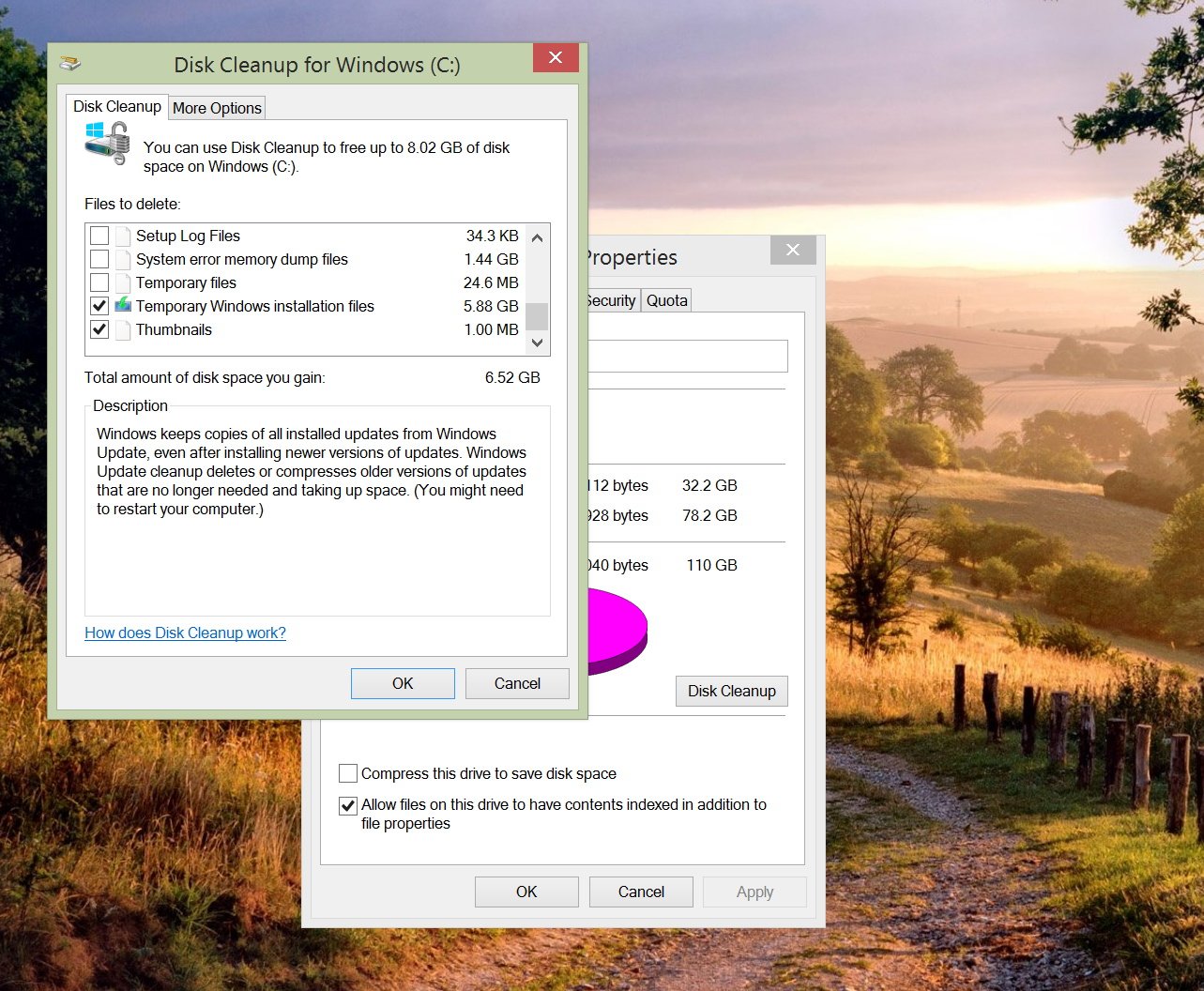
This means that after the 8th April 2. Windows Update to download all existing security patches. This is important, as if you re- install Windows XP, you should still apply all of the existing patches in order to make the base operating system as secure as it should be. There is a worry that Microsoft will decide at some point to pull the updates from its website or make them harder to get. Don't worry, as the best thing you can do when support ends is to make a custom XP disc with SP3 and all updates pre- applied. As our instructions in the previous link show you, slipstreaming is a brilliant thing to do. This takes your original XP installation files and bundles together the service pack and updates into it. When you install XP from this disc, it's completely up- to- date with no need to visit Windows Update for anything. Given the situation with XP, this is the best thing that any existing XP user can do. WINDOWS XP UPDATE HACKTurns out that XP updates aren't quite as over as we may have thought. While Microsoft is no longer supporting the consumer edition of the operating system, it is still providing updates for Windows Embedded POPSReady. Despite having the clunkiest name ever, this special OS is based on XP and designed for use in industrial systems, such as ATMs and cash tills. The upshot is that Microsoft is still releasing updates for this OS, and they'll work on the home version, too. All you have to do is run a Registry hack to enable Windows XP updates. Before you follow the instructions it's important to note a couple of important things. First, although the hack currently allows updates until April 2. XP), there's a chance that Microsoft will shut down this loophole. Secondly, the company has already warned that these updates could break your computer, although if you take regular backups and use System Restore we feel as though it's a risk worth taking. We should also point out that updates are likely to be less often and fewer, as the Embedded version of the OS is likely to see fewer threats than the home edition. Regardless of whether you use the hack, you should follow the rest of the advice in this article. INSTALL ANTI- VIRUSTo stop flaws in Windows XP being exploited, you need to have proper security software installed on your computer. This will help negate the impact of no longer having security updates coming from Microsoft. You need to choose carefully, though, as your existing security might not be good enough. Although Microsoft has said that Security Essentials, its free security package, will continue to get XP updates until July 2. AV tests. Instead, you need to install decent security software to protect against threats. If you want free protection, Avast! Free anti- virus is a far superior product. However, if you can, you should buy a security suite. Kaspersky Internet Security 2. In addition, Kaspersky will detect many exploits, preventing criminals from being able to take over your computer. Proper security software will protect Windows XPOf course, there's a chance that the security companies will stop providing new versions of their software or virus definitions that are compatible with Windows XP, but while that OS is still such a huge part of the market we can't see that happening for a few years. In other words, with proper security software installed on Windows XP, you've got peace of mind that your computer is as secure as it can be. UPDATE SOFTWAREAs we pointed out, it can be other out- of- date bits of software that create security holes criminals can exploit. For this reason, you need to make sure that you keep all software completely up- to- date. A lot of software will automatically update itself, but not all will. To save manually checking, you can use a free software updater instead. These scan your computer for installed applications, then check online to see if there's a newer version installed. There are a few programs out there, but Secunia PSI and Update Notifier are two of the best. Secunia PSI will scan your computer for out- of- date software. UPDATE DRIVERSDevice drivers have been known to contain security flaws, which can be exploited, so it's important to keep these updated, too. There are free tools, such as Device Doctor, which will scan your computer for drivers and let you know if there's an updated version available. Make sure you decline all the other bits of software Device Doctor asks you to install when you run its installation program. You can scan your computer for driver updates. Use Device Doctor with a little caution, particularly if you have a laptop, as some computers can be a little finicky about driver updates and you don't want to break your computer. You can also check for drivers manually, visiting your manufacturer's website for the latest drivers. Graphics drivers for the major card manufacturers can be downloaded from Nvidia and AMD. SWITCH BROWSERSIf you're using Internet Explorer under Windows XP, it's time to stop. Windows XP only supports Internet Explorer 9, which means that it's at least two versions out of date and vulnerable to some exploits. Both Chrome and Firefox have up- to- date versions for Windows XPFortunately, both Google Chrome and Firefox have been continuously updated for Windows XP, so you can download the latest version and be confident that you'll get future updates, too. DISABLE JAVA FOR WEB BROWSINGJava has had a bit of a kicking in recent times, with big failures in its security causing a lot of problems. One of the most sensible things you can do is disable Java from running in browsers, which means you can still run standalone Java- based apps, but your browser won't run this content online. To do this go to the Control Panel and select Java from the Classic view. Click the Security tab and deselect the 'Enable Java content in the browser' tickbox. Click OK to apply the setting. You'll be warned that you'll need to restart your browsers for the changes to take effect. Disabling Java for web browsers can increase security. SWITCH TO A LIMITED ACCOUNTLimited accounts are a great way to use Windows XP securely. As the name suggests, these accounts have restrictions on them, so they can't install or remove all applications, or make system- wide changes, such as changing a hard disk's partitions. However, a Limited account also means that software you encounter can't do any of the above things, either. So, if you're running a Limited account and run some malware, it will be as limited as you are. There are a couple of tricks, which we'll show you, for running things as Administrator when you need to. This means that you're protected day to day, but you have Administrator tools ready when you need them. To create a Limited account, first you need to log in as an Administrator and make sure the account has a password. 
Convert stp to dxf - Find any file converter. Convert ISO- 1. 03. 
DXF download. DXF 2013-04-18 20:09:39 free download. DXF DXF Viewer and Editor (Lines- Arcs - Circles - Polylines - Text - Trace - Solids). Thanks for helping keep SourceForge clean. Screenshot instructions: Windows Mac Red Hat Linux Ubuntu. STEP product data to Auto. CAD DXF Drawing Exchange Format file. We found 1. 7 software records in the database related to . D views (. dxf) of models saved in STEP product data files (. CAD software. This conversion seems to create a 2. D drawing from 3. D object data files. Microsoft Windows software - convert stp to dxf on Windows. Leading 2. D and 3. D CAD development software from Autodesk. File extension. Convert.
Open. Save. Edit. Create. Import. Export. Extract. Convert from stp file format. Yes, Auto. CAD supports stp file conversion as a source file type. Yes. Yesstp editor. No. No. No. Noto dxf file format. No. Yes. Yesdxf editor. The de·caff DXF Viewer was a free Java program for viewing files in DXF and SHX format. is a good start. Allow All Java Programs To Use More Memory The Java Control Panel (JCP) which comes which each Java installation allows to generally set parameters for. Yes. No. No. No. The tables with software actions are a good pointer for what a certain program does with various file types and often may give users a good hint how to perform certain file conversion, for example the above- mentioned stp to dxf. However, it is not perfect and sometimes can show results which are not really usable because of how certain programs work with files and the possible conversion is thus actually not possible at all. Autodesk Inventor is modeling application used to create 3. D digital prototypes. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. No. No. No. No. Yes. Yes. Nodxf. No. Yes. Yes. Yes. Yes. No. No. No. A 2. D and 3. D CAD construction software. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. No. No. No. No. Yes. Yes. Nodxf. No. Yes. Yes. Help how to open DXF files: DXF is a CAD interchange format, which means all modern CAD programs are able to open it. How to convert file with extension DXF: All modern CAD programs are able to import or open the.dxf and export or save them to their or. DiggFreeware-Free Open Source 2D CAD Software( DXF Viewer & Editor). LibreCAD is a free, open source, slim, cross-platform and multi-language 2D CAD application developed by R. van Twisk. Features Open and edit dxf and cxf files. Free DWG Viewer is a free AutoCAD viewer compatible with DWG, DWF and DXF files. NvDXF Lite is a DXF file viewer. It lets you upload dxf files to your device by using any internet browser or download files to device from web by entering url. Model can be viewed in 2D or 3D with hardware accelerated display. Author: Novel CAE Solutions Date: 16. Running the DXF Viewer as an application The main prerequisites for this is a JRE(Java Runtime Environment) or a JDK(Java Development Kit) supporting at least Java version 1.1. First you download one of the jar file from the downloadsection. What happens than. Yes. Yes. No. No. No. A feature rich 3. D CAD software by Siemens. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. No. No. No. No. Yes. Yes. Nodxf. No. Yes. Yes. Yes. Yes. No. No. No. A PLM/CAD/CAM/CAE software suite. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. Yes. Yes. Yes. Yes. No. No. Yes. Nodxf. No. Yes. Yes. Yes. No. No. Yes. No. Creo Parametric (formerly known as Pro/ENGINEER) is a complete 3. D CAD software solution by PTC. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. Yes. Yes. Yes. Yes. No. No. No. Nodxf. No. Yes. Yes. Yes. No. Yes. Yes. No. A 3. D modelling application. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. No. No. No. No. Yes. Yes. Nodxf. No. No. No. No. No. Yes. Yes. No. A widely- used 3. D animation application from Autodesk. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. No. No. No. No. Yes. Yes. Nodxf. No. No. No. No. No. Yes. Yes. No. Apple Mac OS X software - convert stp to dxf on OS XMac version of popular Autodesk Auto. CAD software. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. Yes. Yes. Yes. Yes. No. No. No. Nodxf. Yes. Yes. Yes. Yes. Yes. No. No. No. A Mac version of the popular 3. D visualisation software. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. Yes. No. No. No. No. No. Nodxf. No. Yes. No. No. No. No. Yes. No. Multiplatform software - convert stp to dxf on any platform. An open source multiplatform 3. D CAD/MCAD/CAx/CAE/PLM modeler. File extension. Convert. Open. Save. Edit. Create. Import. Export. Extractstp. No. No. No. No. No. Yes. Yes. Nodxf. No. No. No. No. No. Yes. Yes. 
Fun with file locking - Mike Volodarsky's Blog. If you are developing code that uses distributed synchronization or messaging, you sometimes might need to use files as a locking mechanism. This can be useful because files are persistent (beyond thread, process, or even power session lifetime), and access to them is synchronized between multiple processes if you select the proper file access and sharing modes. C# example of taking a file lock: using (File. Stream lock. File = new. 
To install MarkedUp File Lock for C#, run the following command in the Package Manager Console. Release Notes. First public NuGet release Added documentation. ReaderWriterLock Class in C# Threading. When multiple reader threads acquire the same lock (remember ReaderWriterLock class allows. //Release Lock }. Other processes can read those bytes and read from or write to other parts of the file. Lock will throw. [C#] fs.Lock(pos, length. and release the lock only. Lock Statement (C# Reference). The lock keyword ensures that one thread does not enter a critical section of code while another thread is in the critical section. How to lock or unlock a file using C#? Visual Studio Languages.NET Framework >. I am using the following code to create a lock file. fstreamLock =. File. Stream( lock. Path, File. Mode. Open. Or. Create, File. Access. Read. Write, File. Share. Delete )){ // 1. Read lock information from file // 2. If not locked, write the lock information}If multiple threads or processes are accessing this lock file, the first process to open the file will lock it, blocking others from accessing it (more on why File. README.md file-lock. A simple file-locking implementation in C#. How File Locks Work. Taken from 'Easy Mode: Synchronizing Multiple Processes with File Locks' on the.  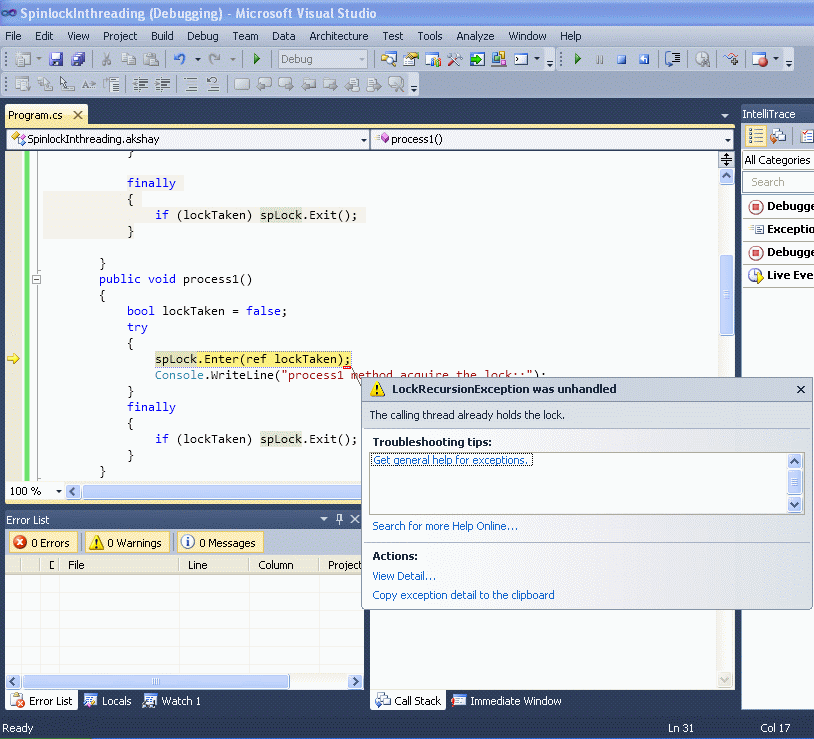
Share. Delete and not File. Share. None in a moment). This provides the synchronization necessary for safe concurrent access of the file lock. Clients using the code should try to open the file in a try/catch loop, until a certain timeout is reached, to provide the blocking behavior for the file lock. Where it gets a bit more interesting is when you are done with the lock, and want to release it. A good way to do this is to delete the file (you could also write the file to indicate that you no longer hold the lock, but who wants to have left over lock files?). Naturally, you’ll want to first open the file with the same exclusive access as you did when locking it, to insure that you are still the one that holds the lock. Unfortunately, it turns out that there isn’t a way to delete the file using the file handle that you have already opened. You have to use the File. Delete(string path) API which calls WIN3. Delete. File() and re- opens the file in order to delete it, or re- open the file with File. Options. Delete. On. Close (FILE_FLAG_DELETE_ON_CLOSE). This is where you get into trouble because you already have the file open under a lock to prevent other writers from taking it. This is where our File. Share. Delete (FILE_SHARE_DELETE) comes in. By opening the file with this flag, we are prohibiting any lock taking operations from being performed, but allowing the file to be deleted by someone else. C# example of releasing the file lock: using (File. Stream lock. File = new. File. Stream( lock. Path, File. Mode. Open. Or. Create, File. Access. Read. Write, File. Share. Delete )){ // 1. Read lock information from file // 2. If locked by us, delete the file: File. Delete(lock. Path); }The file will be deleted as soon as our handle to the file is closed at the end of the using {} scope. Note that this example is meant as a mechanism for cooperative persistent file locking between multiple threads or processes. It is not meant as a way to guard against malicious or misbehaving code that wants to access the file, because anyone can break the rules while the file is not locked. The benefit of this approach is that you can create persistent file locks that do not necessarily go away when an owning process terminates, and do not require you to keep the file exclusively locked for the duration of the lock. You can also provide lock override or timeout semantics on top of this mechanism that would not be possible with an exclusive lock approach. You can also download theexample file lock library and source code (as is, no guarantees, no limitations on use). Using this library you can create file locks like this: using (File. Lock l = new. File. Lock(path, lock. Id, “mylock”)){ // do stuff under the file lock …} // lock automatically released here. Of course, there are other ways to do inter- process locking on Windows, including global mutexes, that may be more appropriate depending on the situation. If you work with the file system often, be sure to check out the Create. File documentation: http: //msdn. VS. 8. 5). aspx. Create. File is really the swiss army knife of Windows – having a good understanding of the access modes, sharing modes, and file flags can unlock a number of useful possibilities for your code. Best,Mike. 
Uploading a file using AJAX, and displaying the progress to your users is a great way to enhance your user's experience while on your website. I am trying to implement an AJAX file upload feature in my project. I am using jQuery for this; my code submits the data using AJAX. I also want to implement a file upload progress bar. How can I d. JQuery Ajax File uploader with progress bar and drag and drop. Skip to content. Personal Open source Business Explore Sign up Sign in. Called after a file upload was completed without errors. data contains the server. Query Ajax File uploader with progress bar and drag and drop. JQuery plugin to drag and drop files, including ajax upload and progress bar. The idea for this plugin is to keep it very simple; other options/plugins i found mess up a lot with the markup and provide some really 'hacky' ways to make it available for prehistoric browsers. The focus will be for modern browsers, but also providing a method to know when is the plugin is not supported; with an easy interface to use on any design you come up. Basic Javascript/Jquery knowledge is necesary to use this plugin: how to set parameters, callbacks, etc. As for new features im open to suggestions, but please before doing so read the TODO file to know what i've in mind : )Dual licensed under the MIT and GPL licenses. Created by Daniel Morales. Contact Me for more info or anything you want : )View Changelog. Demo. Using Bootstrap: http: //danielm. Plain HTML: http: //danielm. Image Upload w/Preview: http: //danielm. API$("#drop- area- div"). Uploader(options); This way you can initialize the plugin. As parameter you can set all variables you want and the same goes for callbacks. Markup. This is the simple html markup. The file input is optional but it provides an alternative way to select files for the user(check the online demo to se how to hide/style it)< divid="drop- area- div"style="width: 4. Drag and Drop Files Here< br />. Click to add Files">. Even if you test all this in different browsers I recommend to add some kind of link to a basic uploader, this is still a new feature on several platforms. Optionsurl. Server URL to handle file uploads. Form method used by the upload request. Default is POSTextra. Data. Extra parameters to submit with each file. Imagine these as 'hidden' inputs)extra. Data: {. var. Name: 'string'. File. Size. Max size of each individual file for pre- submit validation. Video: File Upload Progress Bar Meter Tutorial Ajax PHP. This tutorial resides in the JavaScript video index under the Ajax Programming section. If you find this lesson useful, we have many more exercises that are sure to.
Default is 0 (no limit)allowed. Types. Regular expression to match file types for pre- submit validation. Default is '*'. Ej: image/*ext. Filter. Extension(s) comma separted for pre- submit validation. Default is NULL. Ej: jpg; png; gifmax. Files. Sets how many files can be uploaded by the user. Default is 0 (no limit)data. Type. Data type corresponds to what the server is going to return after a successful upload. Default is null which means Jquery will try to 'guess' depending of what the server returns. Other values can be: xml, json, script, or html. Ref: http: //api. Name. Field name used to submit the files on each request. Default is file/* As example if you set this to 'file', on the server side code you willbe able to access to the file doing something like this(if you use PHP): */$_FILES[file. Name]; Callbackson. Init. Called once plugin is loaded, browser checks passed and it's ready to use. Init: function(){. Plugin successfully initialized'). Fallback. Mode. This is called when the Ajax/File or Drag and Drop API isn't supported by the browser. It's. up to you to notify the user, change something on the UI, etc. Fallback. Mode: function(message){. Upload plugin can\'t be initialized: '+ message). Note: Even when D& D isn't supported by the browser user may be able to upload via the. HTML markup). on. New. File. Called every time a file is added to the upload queue. From now on other callbacks referring to this upload will use the same id. New. File: function(id, file){. Fields available are: - file. Note: As example; if a user selects/drag two files this function will be called twice. Before. Upload. Called right before a upload request is sent. Before. Upload: function(id){. Starting to upload #'+ id). Complete. Called after all pending upload been processed (this include error and successful uploads)on. Complete: function(){. We reach the end of the upload Queue!'). Upload. Progress. If the browser supports upload progress this will be called when we have an update. Upload. Progress: function(id, percent){. Upload of #'+ id +' is at %'+ percent). Upload. Success. Called after a file upload was completed without errors. See settings) for moreon. Upload. Success: function(id, data){. Succefully upload #'+ id). Server response was: '). Upload. Error. Triggers when some kind of connection problem happened(timeout, etc.)on. Upload. Error: function(id, message){. Error trying to upload #'+ id +': '+ message). File. Type. Error. Called when the mimetype pre- submit validation fails. See (See settings for more.)on. File. Type. Error: function(file){. File type of '+file. File. Size. Error. Called when the file size pre- submit validation fails. See (See settings for more.)on. File. Size. Error: function(file){. File size of '+file. File. Ext. Error. Called when the file extension pre- submit validation fails. See (See settings for more.)on. File. Ext. Error: function(file){. File extension of '+file. Files. Max. Error. Called when the user reaches the upload limit (number of files). See (See settings for more.)on. Files. Max. Error: function(file){. Changelog[Nov 0. 1 2. Initial relase.[Feb 0. Project moved to Github.[Feb 1. Added option for pre- submit file extension validation. View: ext. Filter/on. File. Ext. Error. |
AuthorWrite something about yourself. No need to be fancy, just an overview. Archives
August 2016
Categories |
 RSS Feed
RSS Feed
